Spectra: New vulnerability class breaks separation between wireless chips
Researchers from TU Darmstadt and University of Brescia present their results at Blackhat and DefCon conference
2020/08/06
Nowadays wireless technologies are increasingly sharing spectrum—they transmit data on similar frequency bands. This is the case for both Wi-Fi and Bluetooth, but also some LTE bands and harmonics. Since they operate on the same frequency, wireless technologies need to coordinate wireless spectrum access to avoid collisions.
However, the ability to avoid collisions enables a new vulnerability class discovered by Dr.-Ing. Jiska Classen (TU Darmstadt, Secure Mobile Networking Lab) and Prof. Francesco Gringoli (University of Brescia), which enables privilege escalation between wireless components. These new vulnerabilities, named Spectra, show that spectrum coordination allows attackers to escalate their privileges between wireless chips. Thus, wireless attacks on different protocols and technologies become equivalent. An attacker with on-chip Bluetooth code execution can escalate their privileges into the Wi-Fi chip and also execute code on these on modern devices like iPhones, MacBooks, and Samsung smartphones, even with the most recent security patches, because the underlying security problem is in the hardware itself.
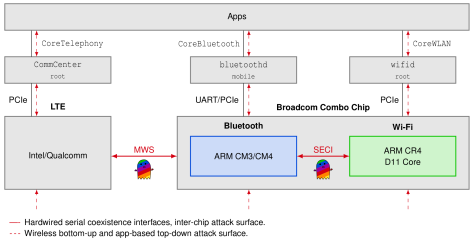
Spectra relies on the fact that transmissions happen in the same spectrum and wireless chips need to arbitrate the channel access. So-called coexistence mechanisms, which arbitrate spectrum access between wireless chips, are the key to high-performance spectrum sharing. For example, they enable streaming a video over Wi-Fi while listening to it with Bluetooth headphones, even if both operate on the 2.4 GHz band. Some coexistence mechanisms can be implemented in over-the-air protocols, however, for nearby chips in small devices with co-located or shared antennas they need to be implemented locally within one device. These coexistence mechanisms are often serial lines within the hardware, which is required to make real-time packet-based transmission decisions. While coexistence should only increase performance, it also poses a powerful side-channel. Moreover, vendor-specific extensions can even lead to code execution. Since coexistence is anchored within the wireless hardware, the operating system cannot defend against these attacks.
Spectra enables new attack paths. While the typical attacks escalate from one wireless chip into the operating system, an attacker can now escalate from the Bluetooth chip into the Wi-Fi chip and from thereon in the operating system. Moreover, issues within the operating system’s Bluetooth daemon now also allow attacking Wi-Fi components. Bluetooth is well-known for having security issues and, thus, is separated from other components—but Spectra allows new escalation strategies.
Prof. Francesco Gringoli, who has been reverse-engineering Wi-Fi chips, and Dr.-Ing. Jiska Classen, who has been exploiting Bluetooth chips, combined their knowledge to build Spectra proofs of concept on Broadcom and Cypress combo chips. These chips are in many popular devices, such as all iPhones, MacBooks, the Samsung Galaxy S series, Raspberry Pis and fitness trackers. While they use these chips to build concrete proofs of concept, the general vulnerability class also affects other manufacturers who were informed during the responsible disclosure process.
Prof. Matthias Hollick, who is leading the Secure Mobile Networking Lab at TU Darmstadt, adds: “These vulnerabilities are fundamentally new. They affect hundreds of millions of devices and chip manufacturers are working on solutions.”
The Spectra proofs of concept break the separation between Wi-Fi and Bluetooth on combo chips, which run on different ARM cores. In general, there are three types of coexistence exploitation:
- Denial of service: One wireless core denies transmission to the other core.
- Information disclosure: One wireless core can infer data or actions of the other core.
- Code execution: One wireless core can execute code within the other wireless core.
The patches that have been rolled out on Android and iOS around March 2020 now prevent attackers from writing to the Bluetooth RAM via the operating system’s Bluetooth daemon. On rooted and jailbroken devices, these patches can be deactivated. Unpatching these patches shows that the chip-based escalation has not been patched. An attacker with control over the Bluetooth chip can still gain code execution within Wi-Fi as of iOS 13.6 on an iPhone 8 (most recent in August 2020), macOS 10.15.5 on a MacBook Pro 2019/2020, and Android 9 with a June 2020 security patch level on a Samsung Galaxy S8. More recent versions are likely still affected by these attacks as the root cause of Spectra attacks lies within the hardware, however, the incomplete daemon-only patches make further patch verification harder.
While Spectra has comparably strong attack prerequisites, such as observing precise packet timings or even executing code on a wireless core, it is hard or even impossible to mitigate without significant performance drawbacks. Other manufacturers sometimes combine multiple wireless technologies within the same core, and there are a lot of unknown proprietary coexistence mechanisms. Thus, users who want to be secure against wireless attacks should consequently disable all wireless communications and not just one wireless technology.
Contact
For technical questions regarding Spectra, please contact Dr.-Ing. Jiska Classen.
Please send press requests to Ann-Kathrin Braun.
Further information